| « Back to article | Print this article |
Downloading a popular app on your smartphone? BEWARE!
Scared personal data on your smartphone could be misused when you allow apps to access your data? You should be.
While there are checks built into the apps ecosystem, checking veracity of apps you install on your smartphone is YOUR responsibility, Himanshu Juneja tells you how to negotiate those dreadful app permissions!
Every mobile phone user by now must have seen the prompt screen asking for permissions while installing an app. These permissions are a regular affair and one cannot proceed to install an app without agreeing to them.
There always have been concerns and noises raised by people regarding this.
And rightly so too! Any smart user ought to ask questions, more so when the app might be asking to dig into a device which, in all the probabilities, will be holding personal and important information. While the situation really cannot be helped and a user has to 'allow' them to enjoy the services of the app, the situation begs the question: Should you be concerned while agreeing to all these permissions?
Answer is: Maybe yes.
Take note, that in the reply above, the word 'maybe' is to be stressed upon and not the latter part. The good news is that the cause for asking the permissions is generally valid, and your data is safe as long as the app is coming from a verified source/developer.
For further clarification, we need to take a look at the reasons for the need for these permissions to be popping up in the first place.
Dear readers, how do you deal with these permissions? Post your valuable advice on the message board below!
Reader Invite
Are you a gadget/gaming wizard/afficianado? Would you like to write on gadgets, gaming, the Internet, software technologies, OSs and the works for us? Send us a sample of your writing to gadgetsandgaming@rediffmail.com with the subject as 'I'm a tech wizard/afficianado' and we will get in touch with you.
Downloading a popular app on your smartphone? BEWARE!
Apps (Short for applications) are pieces of software intended to carry out tasks. For these tasks to be completed, there would be certain prerequisites which need to be fulfilled. The apps, hence will ask for approval in the form of these permissions just to work, or initiate actions which are essential for them.
For example, apps might be designed to ask for your account information/phone number first up which might raise a bit of a concern, but this generally is a way to confirm authenticity, ie the app has not been pirated.
Some apps, for example Gmail, Google +, Facebook etc ask for truckloads of permissions owing to the nature of the their basic functioning.
Other apps, free in nature, will be asking for permissions like internet access along with other permissions in order to display ads of their sponsors/partners to fulfill their end of the contract (The paid apps may well ask for internet access as well, but for different functions entirely).
An app can ask for plethora of permissions, details for which can be sought as described later, but users commonly need to look out for permissions which are directly going to access personal info (Permissions like Read contacts, Write Contact data etc), permissions which might cost money like initiating outgoing calls/SMS etc. These permissions must be granted to only those apps which justify the usage.
Also, another aspect which the user specifically needs to be cautious about is when the app really is trying to invade your device's system level access. What we call as a situation when an app requires the phone to be rooted in order to install itself.
Rooting is the procedure, by which a user unlocks the system level access of the device. This access must be enabled by the users if they have full knowledge of their device and their subsequent actions, as one mistake can brick the device, rendering it useless. Due to high chances of the device getting damaged, usually the root access of the device is not allowed by the device manufacturer.
An application like Titanium backup is justified in asking root level access, as it will be performing tasks at the system level. But if some basic app like for example a Calculator asks for root level access, then it is definitely not expected or justified.
Dear readers, how do you deal with these permissions? Post your valuable advice on the message board below!
Reader Invite
Are you a gadget/gaming wizard/afficianado? Would you like to write on gadgets, gaming, the Internet, software technologies, OSs and the works for us? Send us a sample of your writing to gadgetsandgaming@rediffmail.com with the subject as 'I'm a tech wizard/afficianado' and we will get in touch with you.
Downloading a popular app on your smartphone? BEWARE!
What can be done?
1. Read the descriptions
A user should make a healthy habit of at least paying attention to the details mentioned of the permissions asked. These descriptions will help users to corelate and equip them to ask questions about the justification of such requirements. If a user can link the permission to some feature which is just and a necessity, then it's a green signal.
In order to garner more info and clarity about the detail of the permissions, a user can visit the market page of the app and go through the description provided. Also, the privacy policy stated by the developer, or the developer's website is always there to provide further clarity.
If everything fails, a responsible developer's email always comes in handy. Firing a mail to the developer is never a bad idea, however this option should not be abused and only be exercised after due research and homework.
Preferring verified and reputed developers only
This is pretty much a given that in a world which is equipped with social media websites/tools no serious developer would like to jeopardise it's image.
Although there might not always be elaborate screening procedures while enlisting apps, every app is to bear a 'self sign' of the developer, so that in case of any foul play, market places will not only remove the app, the developer could be tracked and might get blacklisted as well. Due to this check, the chances of losing customers will always loom on any serious developer. Losses on financial front due to app getting removed could be significant as well.
Dear readers, how do you deal with these permissions? Post your valuable advice on the message board below!
Reader Invite
Are you a gadget/gaming wizard/afficianado? Would you like to write on gadgets, gaming, the Internet, software technologies, OSs and the works for us? Send us a sample of your writing to gadgetsandgaming@rediffmail.com with the subject as 'I'm a tech wizard/afficianado' and we will get in touch with you.
Downloading a popular app on your smartphone? BEWARE!
2. Check reviews
Another big advantage of downloading apps from a well known source is the review section.
Any bug which might be there, even with newer versions of the same app, will find a mention in the review section, thereby alerting any potential downloading or updating of the app.
3. Keep a check on your app permission
Thankfully enough, there are few apps out there in the market like Play Store to monitor the permission and data access carried out by apps.
For example:
1. Pocket permission
Although a paid app, this is a comprehensive guide for the interested users/developers. It provides the details about the nature and meaning of the permissions asked, and what kind of data flows once the permission is granted by the user.
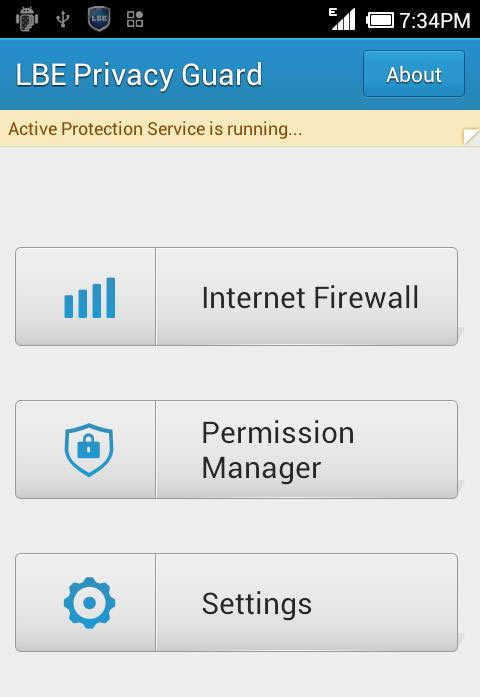
2. LBE privacy guard
At the risk of crashing an app, a user can disallow the access of data by an app. The privacy guard sends in a notification when any app tries to access your data, and allows the user to stop the same.
This app requires the phone to be rooted, and this one is definitely justified in asking so.
Dear readers, how do you deal with these permissions? Post your valuable advice on the message board below!
Reader Invite
Are you a gadget/gaming wizard/afficianado? Would you like to write on gadgets, gaming, the Internet, software technologies, OSs and the works for us? Send us a sample of your writing to gadgetsandgaming@rediffmail.com with the subject as 'I'm a tech wizard/afficianado' and we will get in touch with you.