 | « Back to article | Print this article |
Six pieces of malware present in the laptop had truly terrible track records.
It's estimated that these six programs have logged combined damages of $95 billion between them, says Devangshu Datta.

Art installations can use objects ranging from the mundane to the grotesque or exotic.
The Persistence of Chaos is deceptively boring at first or second glance.
PoC is a standard off-the-shelf laptop, with 11-year-old specs, running an old operating system.
That hard drive, however, contains six of the most dangerous computer programs of all time.
PoC was billed as the most dangerous PC in the world when it was sold at auction for $1.345 million.
Another unit of that same laptop model would be available for less than $100 second-hand.
What's more, the buyer will never use PoC because it was only sold on the undertaking that it would be permanently 'air-gapped' -- it will never be connected to a local network, or to the internet.
The PoC is nominally a Samsung NC10-14GB 10.2-inch laptop.
That's a mid-range model launched around 2008.
It runs on Windows XP (Service Pack 3), and is loaded with six different malware.
Win XP was released in 2001, before Microsoft launched successors Windows 7, Windows 8, 8.1 and Windows 10.

The laptop was loaded by artist Guo O Dong who was commissioned by cybersecurity firm Deep Instinct to pick and choose his preferred weapons of cyber-destruction.
Dong chose to load six malware programs, including ILOVEYOU, MyDoom, SoBig, WannaCry, Dark Tequila, and BlackEnergy.
It is illegal to run malware for operational purposes (and some of those programs wouldn't work on modern networks anyway).
The PoC will be a conversation piece, sitting somewhere in a display cabinet running a slide show that tells viewers why it's the most dangerous PC in the world.
Computer malware has caused huge amounts of damage over the decades.
These six pieces of malware have truly terrible track records.
It's estimated that these six programs have logged combined damages of $95 billion between them.
Each one used what was then innovative methods of getting into systems.
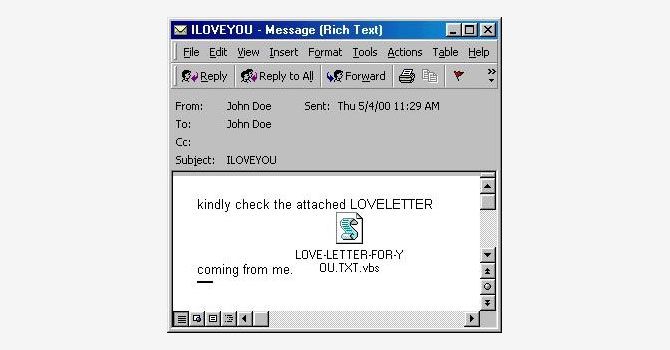
The ILOVEYOU virus was released in May 2000.
It was an e-mail with the header 'I Love you', or variations thereof, and an attachment that read 'Love letter for you'.
The attachment was a program written in visual basic.
The extension '.vbs', which exploited a windows quirk that hides known file extensions.
When users clicked on it, it overwrote local files and sent copies of itself off to every e-mail address on the machine.
It infected millions of computers, causing an estimated $6 billion in damage.
The perpetrators, two Filipino programmers named Reonel Ramones and Onel de Guzman, escaped prosecution because the laws of the time didn't cover their offence.
MyDoom (or Novarg, or W32) is a worm that creates backdoors in the target, allowing for the system to be taken over.
It was also spread through e-mail and used to set up networks of slave computers that coordinated in Distributed Denial of Service (DDoS) attacks.
In a DDoS attack, a network is overwhelmed by a huge number of computers demanding to connect at the same time.
It was probably created by a Russian programmer with a grudge.
While the original version was discovered in 2004, variants continued to be used in DDoS attacks for many years.
SoBig was another worm circulated through e-mails circa 2003.
It could copy files, e-mail itself to others, and damage software.
Microsoft still has an outstanding reward offer of $250,000 for information leading to identification of the creator.
WannaCry was a pioneering ransomware cryptoworm.
It encrypted data and set up backdoors on systems.
The malware is believed to have been used on multiple attacks across 150 nations.
It almost crippled the UK's National Health Service and caused over $4 billion in global damages.
Dark Tequila is phishing malware.
It steals bank credentials and sensitive corporate data.
It's believed to have cost billions in the phishing attacks that followed in its wake.
BlackEnergy is perhaps the most fascinating of this dirty half-dozen.
It was discovered in 2007.
It's a rootkit that is near undetectable, since it pretends to be part of the operating system.
The original version was probably designed by a Russian hacking gang.
Later variants have been used by all sorts of people, including at least two national security agencies in cyber-warfare.
BlackEnergy can be used to take over machines, or to execute destructive programs.
A version of it took down the power grid of the Ukraine in 2015.
Other versions are suspected to have been used by North Korea.
Modern anti-malware programs will detect these programs.
But, of course, there are successors.
The principles of staying safe remain the same.
Avoid opening e-mail attachments from people you don't know; avoid downloading programs from untrusted sources; don't download pirated video, music and PDF files.
This is easy to advise and hard to practise on a 24x7 basis.
Sooner or later, somebody will create a PoC version II and that will feature malware that has caused at least as much damage.
*Kindly note the images have been only posted for representational purposes.
